User Mapping between Windows and Linux
Anvil stores a unified permission structure in its file system, enabling tight integration between Windows ACLs and NFS permissions. There is no option to choose what is stored, or to prioritize one over the other – the ACLs are simply mapped to NFS permissions whenever needed.
Anvil uses Active Directory as the source for mapping between the two environments. Anvil will read Windows credentials from Active Directory and also fields like uidNumber and gidNumber for the purpose of mapping between an identity in Windows and Linux. For Group Membership when files are created, Anvil will map to the Primary Group assigned to the user in Active Directory.
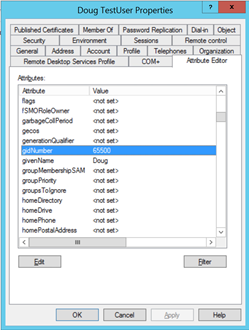
A common UID/GID is required for user mapping to work, in other words, if you user has UID 5555 on the Linux client, 5555 must be entered in the uidNumber field in Active Directory to be able to do a successful mapping. The following images provide examples of a UID and GID.
The client computer should be connected to the same directory service, Active Directory being the most common. For Windows this is standard however for Linux this may not always be the case. Please follow the instructions for the respective Linux platform to join it to Active Directory. It is recommended (but not required) that the Linux environment is connected to Active Directory, Linux environments can be configured with other sources that provides identity to the user.
Default Behavior
The default behavior without user mapping configured will make the environments look disconnected. For example, when saving a file from Windows, the default user of UID/GID 65534/65534 is used. This typically maps to nfsnobody on most Linux systems and is the owner of files and directories. This happens because the file was not saved with a UID/GID that is recognizable by Linux.
Mapping the UID and GID within the Same Active Directory Domain
In Active Directory, each user and group object can also be configured with a UID and GID mapping. This allows for Linux users with their own UID/GID’s to work on files they own and perhaps most importantly, be a part of groups in Active Directory. They are called uidNumber and gidNumber in the Active Directory object as seen in the Figures above.
If these parameters don’t exist, please consult your Active Directory administrators on how to create them.